With almost a decade under its belt, NMap has grown into an indispensable utility for ethical hackers, pen testers & network pros alike. This NMap tutorial provides a brief background, install instructions & a walk-through of its most crucial functions.
Nmap is short for "Network Mapper" and it was originally crafted in C by Gordon Lyon (aka Fyodor). Without venturing too far into the "technical weeds", Nmap utilizes raw packets to probe ports on network devices. Think of it like echolocation for networks. Shooting packets to specified locations & listening for responses provides intel on hosts, ports, services, operating systems, hardware, vulnerabilities & potential exploits. Some may think of it as a hacking tool, but it's more accurate to think of it as a recon tool. While it does supplement more complex tools like Metasploit, an average developer can get it up and running in minutes - so let's get cracking on the installation.
Install Nmap
Like most low-level tools, Nmap is best run from the command line. However you choose to install it, it'll come equipped with its own GUI interface app named Zenmap. While Zenmap can make a handy set of training wheels, we'll cover it last since it's just a usability aid. Moreover, knowing how the tool functions is a large part of getting the most out of it. Select your preferred means of installation below, open it up, & we're ready to get rolling.
- Linux, Mac OS, Windows, & More: Select your OS from the official Nmap page, unzip, & install. (Download)
- Tarball (bzip2): You can now download, extract, & install the latest tarball directly. (Download)
- Source: If you like command line, snag Nmap with this quick snippet.
sudo apt-get install nmap
A Few Clutch Nmap Commands
Let's start by acknowledging that Nmap can be used for mischief. Although network scanning isn't illegal, it is frowned upon by ISPs & will draw attention if abused. Use the techniques in this Nmap tutorial on servers you manage & familiarize yourself with the admin response protocol. This will give you time to understand the intricacies of port scanning while also giving you the practice of remaining unseen. When it comes to use, Nmap is pretty intuitive - just keep in mind the command layout will always be nmap [ <Scan Type> ...] [ <Options> ] { <target specification> }. We'll take that, run through six bite-sized tasks, & by the end of it, you'll have a solid grasp to work from. Let's start with the simplest query first.
- Basic IP / Domain Scan (ipv4): From a bash screen simply type
nmapfollowed by an IP or domain name to query that location. You'll receive a response listing the routing, port topography, and status of commonly used ports (Be sure to note which ones are "open"). If you'd like to scan multiple addresses, just include a space between them. Couldn't be easier.nmap 10.0.0.1
- TCP Scan Open Ports: Including
-ptells Nmap that you're only looking for specific ports (1-65535),-sVprobes open ports for service version, and-sSinstructs Nmap to utilize a TCP SYN scan. While this combination of variables might not make complete sense at first, the more important point is to see how you can string along variables to get more in-depth with your probes.nmap -p 1-65535 -sV -sS 10.0.0.1
- Scan a List of Addresses: If you have a few locations that you'll need to keep an eye on, simply place them all in an unformatted text file with each address on a new line and call them with
-iL. This directs Nmap to the relative location of the text file and it'll take care of the rest.nmap -iL /local/directory/yourlist.txt
- Service Detection: Every available port will return one of six responses (open, closed, filtered, unfiltered, open|filtered, or closed|filtered). Let's say you found an open port you'd like more info on, you can probe ports for more info with
-sVand isolate your scan to just one port by suffixing it on the IP. In this example, we'll look into a default FTP port (22).nmap -sV 10.0.0.1:22
- Zombie (Idle) Scan: We're gathering good intel here, but we are being pretty obvious about it. If a sys-admin on the target network notices a ton of pings coming from the same location, they'll figure you're up to something. So we'll try to run that previous scan again, but this time we'll use
-sIto tell the target pings are coming from a different source.nmap -sI -sV notmyrealnetwork.org 10.0.0.1/22
- Decoy Anonymity: Idle scans are handy, but they do have their limitations. You're trying to pass a lie... Meaning you could be traced and uncovered. Sometimes the best place to hide is in public. Using multiple decoys with
-Dis another great method of obscuring a ping source. This doesn't mean you can't be traced, it just means you'll be one of a group... Plausible deniability.nmap -n -Ddecoy-ip1,decoy-ip2,your-own-ip,decoy-ip3,decoy-ip4 remote-host-ip
- Scan Firewall with a Spoofed Mac Address: Another unique personal identifier that you'll want to disguise is your own Mac Address. Using the
--spoof-maccommand you can cover that base, while you using a little TCP quirk via-sNto query for details on the targets firewall setup:nmap -sN --spoof-mac notmyrealmacaddress 10.0.0.1
Wanna Get Fancy? Here's a Comprehensive Nmap Command List PDF
Wish you had a comprehensive list of all your Nmap commands so you don't need to be surfing the web while scanning? Don't worry, we put them all on a handy little command list PDF for you. These Nmap commands are current as of the date of post and we'll try to keep them updated as needed although Nmap doesn't change too often. Download Nmap Command List PDF
Reading Port Scan Results
If you're not familiar with basic network concepts, the results that are printed out might look like gibberish. Although explaining the intricacies of network design is outside the scope of this post, we'll run through a basic response so anyone noob can start putting this data to work. For this example, we'll print a result from a quick scan on the Nmap website... because irony is sort of awesome.
Starting Nmap 7.31 ( http://nmap.org ) at 2016-12-08 00:46 EST
Interesting ports on 45.33.49.119:
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp closed telnet
25/tcp open smtp
80/tcp open http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp open https
445/tcp closed microsoft-ds
3389/tcp closed ms-term-serv
Nmap done: 1 IP address (1 host up) scanned in 3.31 secondsThe first two lines simply identify the Nmap version, the date, and the port we're querying. After the associated headers you'll start to get the useful data. If you're not already familiar with which services are defaulted on certain ports, this IANA chart covers them fairly well. While you can extend your port scan to less commonly used ports, these 10 will give you a solid lay of the land. If you're looking at your own server those needs obviously depend on your usage, but as a general rule, you should make sure any ports you're not commonly using are closed. You should also try to exclude your port usage to the most secure options possible (SSH over FTP, HTTPS over HTTP, etc.). If you're not sure what a port is used for, use that previous link or Google the port number. In most cases, your server will be defaulted and also keep in mind that you'll likely need root access on a server to adjust this configuration. If you can, it's worth tightening these up though... you'll be severely minimizing your potential risk footprint.
Need a GUI? Here's a Quick Zenmap Tutorial For Ya.
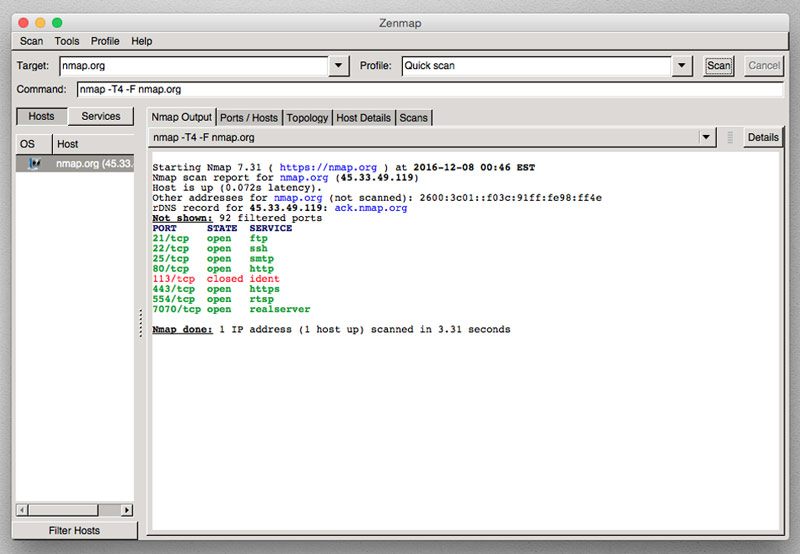
If the command line is still a little foreign to you, don't worry - Nmap comes packaged with its GUI'ed version named Zenmap. From the command line, you'd just type sudo zenmap or just open the app and you have the same basic functionality as on the command line. There are two great features any Zenmap tutorial should point out, but for basic usage just include the domain or IP into the target field, select the scan type, and click scan. The first clutch piece of Zenmap is something I wish more deep-level tools would include, a command field that specifies exactly what you're doing. You can learn how Nmap is functioning just by playing around on a few scans and watching how your commands change. The other clever part of Zenmap is the graphical "Topology" results tab. This gives you an over-the-top view of your recent scans and a useful reminder of where your potential points of entry may lay.
Using Nmap in the Field
As you might imagine, you'll want to take precautions when using Nmap on a project. Although this is certainly an oversimplification two methods of approach that will help you avoid raising too many sysadmin red flags. The first is to disguise your location, like in the Decoy command example above. The other precaution would be to space your pings out with a command like -T or --scan-delay. Any admin that sees a slew of pings coming from a single location will be on guard, but spacing that timing out provides solid cover. Even if your target is logging heavily, it would take them quite a bit of effort to tell who you are and by then you've likely completed your task.
We hope you've found this Nmap tutorial useful & we're sure it'll be a handy tool for future projects. As previously mentioned, make sure you're using it properly & ethically (especially when starting). If you have any tips on other ways beginners can learn Nmap, please send them through your favorite social network & we'll make sure to include helpful additions on future updates. If you've found this post handy or know someone else that would, please share & as always - Thanks for stopping by.